This is a white paper aimed at showing how SSH tunneling can be used to encrypt data as it is transmitted over a network. The network may be on a LAN or a WAN.
Data traffic is very like an ariel view of traffic on a road. The data streams from one location to another. While the vehicle is outside it can be seen. Once inside a garage or building it is no longer visible.
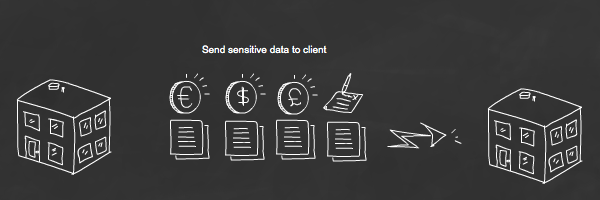
Now consider a very different picture. What if sensitive data was etched into the roof of each vehicle. For example, a username and password, account information, credit cards etc. The view while pretty below might not be so pretty to a network administrator.
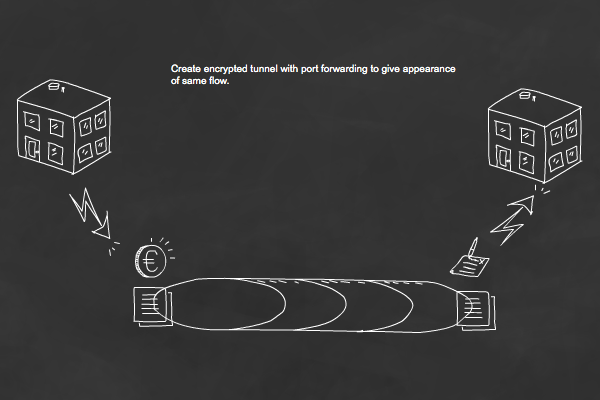
Well you may ask what can we do about it? In the real world to hide the vehicles from an ariel view we could force them into a tunnel and out at the other end directly into a garage or building. Their entire journey is masked from view. Data traffic may also be redirected into an encrypted tunnel and into a server, masking their content from any lurking eyes.
SSH provides this ability to create an encrypted tunnel, with port forwarding. The process is very much like redirecting traffic from the main road into a tunnel and then back onto the main road at the other end so that stream gives the appearance that there has been no redirection.
This same technique can be used in MySQL applications to hide the data stream as it is transmitted over the network in an encrypted tunnel using SSH. The advantage of this type of solution is that the contents are encrypted, however, the encryption and decryption process adds to the overall CPU consumption and data throughput. The next section shows the process involved in setting up the tunnel on a Windows and Linux/Mac OS X machine to access a MySQL database.
Click here to read on how to setup a SSH tunnel on UNIX/Linux/Mac OS X and on Windows.